When the world learned of the WPA2 Wi-Fi vulnerability, some shrugged it off as “just another security flaw.” Here’s why ignoring this one is a big mistake.
 Wi-Fi Protected Access 2 (WPA2) is the current industry standard. That’s right, the standard. In other words, it’s everywhere. WPA2 networks, in fact, are what most of our Wi-Fi-connected devices are using (and have been since 2004). Those networks have been considered uncrackable until now.
Wi-Fi Protected Access 2 (WPA2) is the current industry standard. That’s right, the standard. In other words, it’s everywhere. WPA2 networks, in fact, are what most of our Wi-Fi-connected devices are using (and have been since 2004). Those networks have been considered uncrackable until now.
WPA2 uses cryptographic protocols to secure traffic on Wi-Fi networks. The best-known WPA2 control is strong encryption.
But, it turns out, they’re actually quite vulnerable to cryptographic attacks, which give criminals an open door to millions of connected devices – if they’re not patched.
The flaw in WPA2’s cryptographic protocols – nicknamed “KRACK,” short for Key Reinstallation Attack – can allow hackers to read and steal data on a Wi-Fi network. The bug even leaves room for an attacker to manipulate the data or inject new data into a Wi-Fi network. That means criminals can steal passwords, intercept financial information or even manipulate commands to send money to themselves.
This is very bad news for people sending sensitive information over a Wi-Fi connection – which is pretty much everyone.
For individuals, the fix is relatively straightforward. All they need to do is update their system by downloading the patch.
For organizations, it may not be that simple because of the number of people and devices impacted. This is especially for organizations that aren’t prepared for circumstances like these. So how can your organization be better prepared for what is sure to be an increasing number of discovered system flaws and vulnerabilities?
Below are three things you can start today to help.
- Be aware. Have a process for staying up-to-date with the latest tech news so you know when vulnerabilities and other security issues occur. One good place to check on a regular basis is the US CERT vulnerability database. Make it a strategic priority to stay current and report back to your chief technology officer or chief information security officer. This can no longer be a side job or an “as-you-have-time” task.
- Have procedures. Thoroughly documented and tested (through doing table-top exercises, etc.) procedures should outline how you will address vulnerabilities immediately upon discovery. A lack of procedures will cause panic, confusion and wasted time when swift action needs to be taken to address vulnerabilities. The procedures should address who is responsible for what and how patches will be pushed out throughout the organization.
- Follow the procedures. Once your organization’s procedures are in place, it’s important your employees are aware of, trained on and held accountable to them. Educate staff at all levels (that includes your busy chief executives!) on not only the importance of sticking to procedures, but also their ultimate reason for being. When there is a culture of appreciation for procedures, staff look on them with gratitude, rather than annoyance. Policies and procedures aren’t just about compliance; they exist to allow the organization to run smoothly, efficiently and, most importantly, to manage information risks as effectively as possible.
Whether pushing out a security patch to five or 5,000, being aware of the latest tech news and following thoroughly documented policies and procedures will help you address security issues faster and manage your security program more efficiently.
If you need help getting started, send me an email at rebecca@simbus360.com.
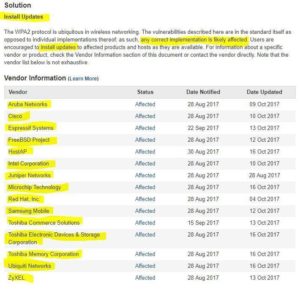
Impacted Vendors
Here are some of the vendors known to be impacted by the WPA2 vulnerability so far. Update your systems as soon as the security patches are released.